Preventing Recently Disclosed Attacks Against AI Agents: Cursor & VS Code
A Wake-Up Call
According to Dark Reading, Cursor was compromised through a malicious extension that injected a harmful payload capable of exfiltrating sensitive data.
Sound familiar? Consider these attack vectors:
- • A malicious extension injecting attack payloads
- • A rogue MCP server implanting malicious payloads
- • Remote code injection executing payloads
These are the same problems we've faced with web browsers for decades. The parallel is clear:
AI agents are the new browsers, and MCP servers are the new web servers.
Netzilo AI Edge & Layered Defense for AI Agents
We designed Netzilo AI Edge with this new threat landscape in mind. Here's how its multi-layered defense architecture can prevent attacks like the Cursor compromise—right out of the box.
Layer 1: AI Detection and Response (AIDR)
Similar to EDR (Endpoint Detection and Response) solutions, Netzilo AI Edge includes an endpoint component. Unlike inefficient remote gateway or cloud-based solutions, it monitors local MCP calls in real-time—including stdio-based servers such as filesystem and Node.js-based tools—directly on the endpoint where attacks occur.
Key capabilities:
Real-time behavioral analysis using both static and dynamic detection methods
Tool call chain interception and advanced analysis, including enforcement of Meta's Rule of 2 (for details, see our blog on AIDR: Detecting and Containing AI Agent Threats)
MCP reputation analysis with the ability to lock down MCP server usage to approved/whitelisted sources only
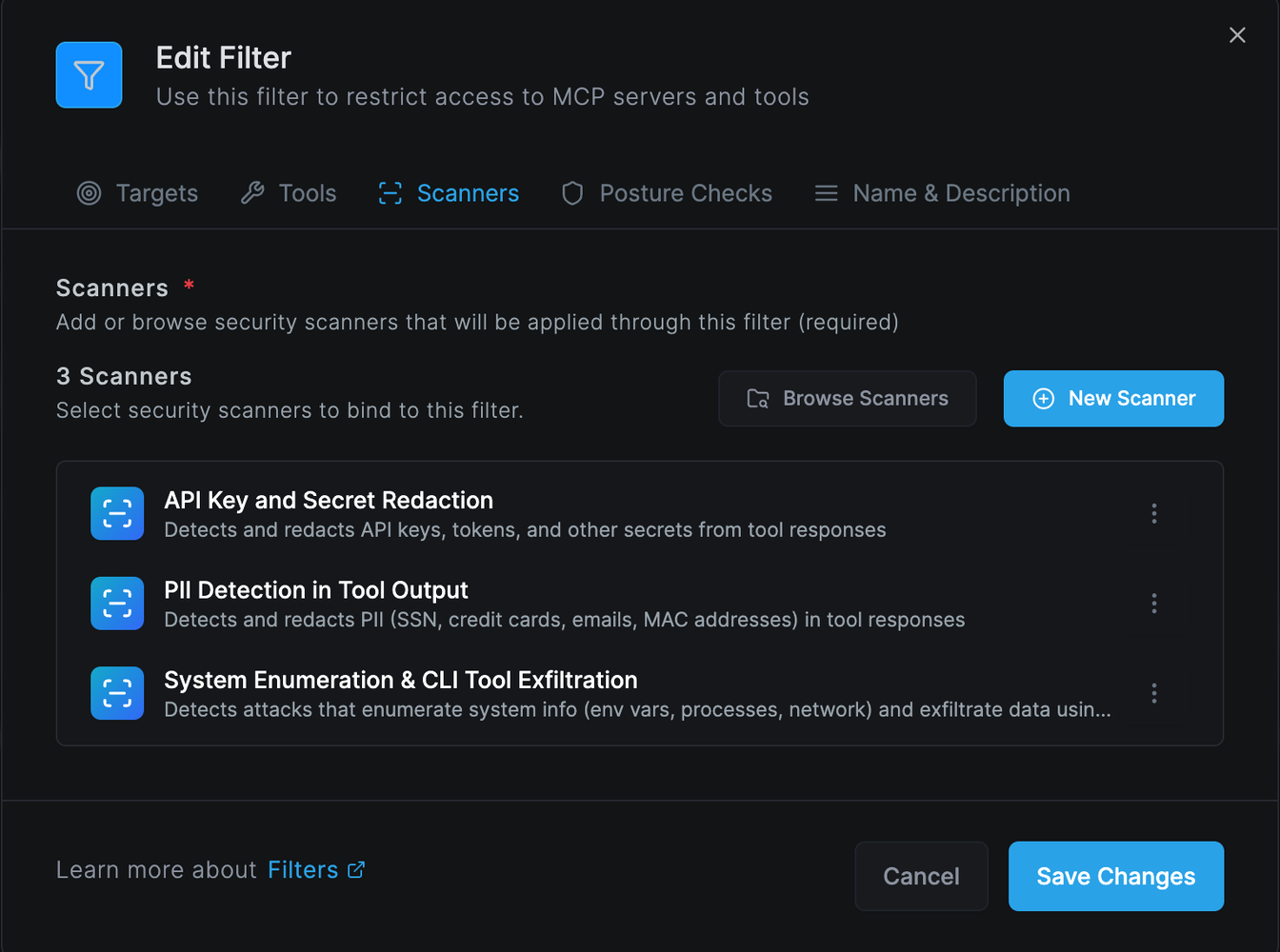
AIDR Behavior Analysis Rules

Enforce Sanctioned AI Tools/MCP Servers
Netzilo AIDR is the only endpoint-based agent behavior analysis system capable of intercepting and analyzing complete tool call chains with this level of sophistication.
Layer 2: AI Agent Isolation
Browser isolation has long been used as a layered defense against attacks on traditional browsers. However, until now, no such solution existed for "the new browsers"—AI agents.
Netzilo Workspace leverages local isolation technology to quarantine AI agents from the rest of the system and the broader enterprise network. This containment approach prevents lateral movement and limits the blast radius of any successful compromise.
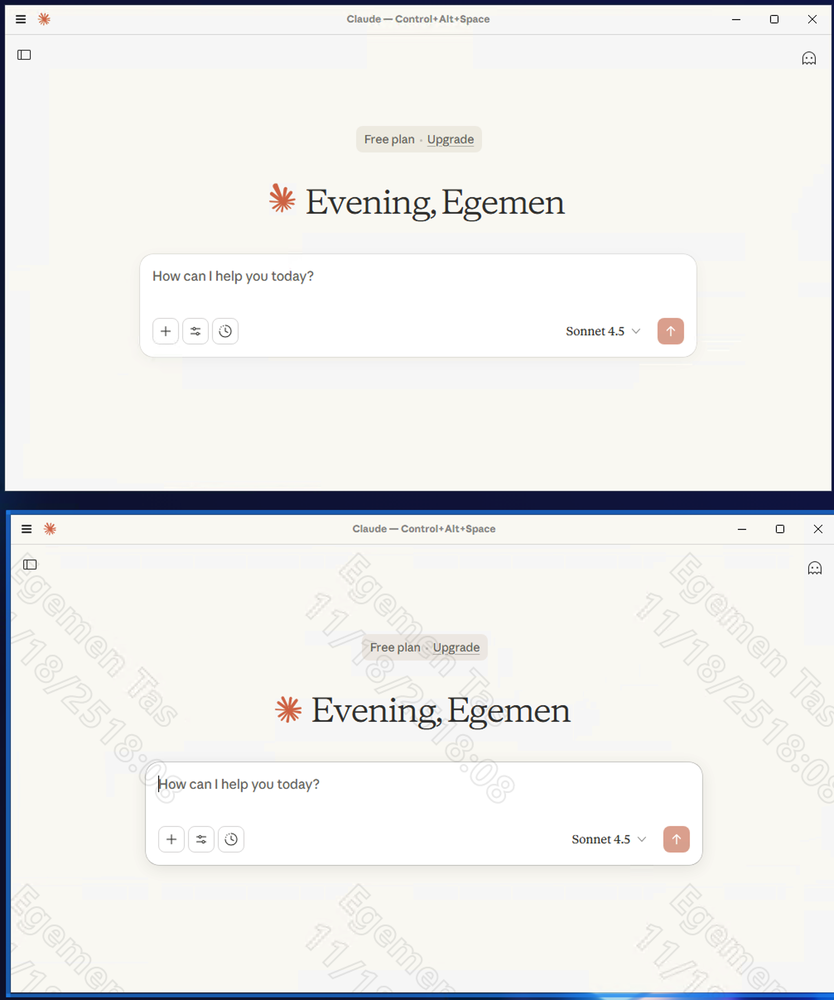
Claude Desktop - Standard vs Isolated in Netzilo Workspace
Layer 3: Endpoint Security Posture Enforcement
With Netzilo AI Edge, endpoint security posture can be enforced for every AI agent activity. This enables zero-trust enforcement with questions like:
- Can the AI agent download files from corporate SharePoint while DLP is disabled?
- Can the AI agent access corporate MCP servers if the endpoint's integrity has been breached?
- Can the AI agent access GitHub code repositories while unsanctioned MCP servers are in use?
These novel zero-trust capabilities bring enterprise-grade security controls to AI agent operations—a critical capability gap in today's security landscape.

Agentic Security Posture Enforcement
The Bottom Line
As AI agents become increasingly integrated into enterprise workflows, they inherit the same attack surface that web browsers have carried for years. The difference? AI agents have direct access to sensitive code, data, and infrastructure—making the stakes even higher.
Netzilo AI Edge provides the comprehensive, layered defense architecture needed to secure this new frontier.
Ready to secure your AI agents?
Give us a nudge if you'd like to get your hands on Netzilo AI Edge.